The recent ransomware intrusion of a major US gasoline pipeline operator was the work of an affiliate of DarkSide, a ransomware-as-a-service ring that has been responsible for at least 60 known cases of double-extortion so far this year. DarkSide has struck several high-profile victims recently, including companies listed on the NASDAQ stock exchange. But the disruption of Colonial Pipeline’s network led to the company shutting down its operational technology (OT) network as well—effectively cutting off a majority of the gasoline supply to the eastern United States.
Colonial Pipeline’s shutdown is not the first critical infrastructure issue triggered by a ransomware attack. Last February, a US-based natural gas facility was shut down for two days by a ransomware intrusion that spread to its OT network. And DarkSide has not avoided these types of companies, either, hitting a Brazilian energy company earlier this year. But the Colonial incident has potentially greater real-world impact—and has apparently made DarkSide’s operators more notorious than they’re comfortable with.
The Sophos Rapid Response team has been called in for incident response or to intervene during an attack involving DarkSide on at least five different instances in the past year.
Coming over to DarkSide
DarkSide emerged last summer, gaining notice with its purported “honor among thieves” approach: the gang claimed to have a code of conduct that forbid targeting industries and non-profit organizations connected to the public interest.
The ring has struggled to keep its “honorable” reputation, using their leak site as a platform to counter bad news. When ransomware recovery company Coveware warned that DarkSide’s use of Iranian hosting posed potential peril of sanctions violations if companies paid them, DarkSide’s operators posted a “press release” denying they used any Iranian IT services. The Colonial Pipeline attack again has the DarkSide gang backpedaling, pleading in a post on their web page that they are “apolitical” and that their goal is “to make money, and not creating problems for society.”

The gang previously promised to spare healthcare organizations, as well as others involved in vaccine distribution, because of the negative attention such attacks could potentially bring from within the gang’s home country. Because of the way DarkSide operates, it’s not clear how much control the keepers of the DarkSide brand have over the affiliates who do the actual work of breaking into networks and launching their ransomware.
DarkSide follows in the footsteps of double-extortion ransomware operators such as REvil, Maze, and LockBit—exfiltrating business data before encrypting it, and threatening public release if the victims don’t pay for a decryption key. Like those other targeted operations, DarkSide makes hefty ransom demands. In one case Sophos Rapid Response worked on last year, the ring demanded $4 million (which went unpaid).
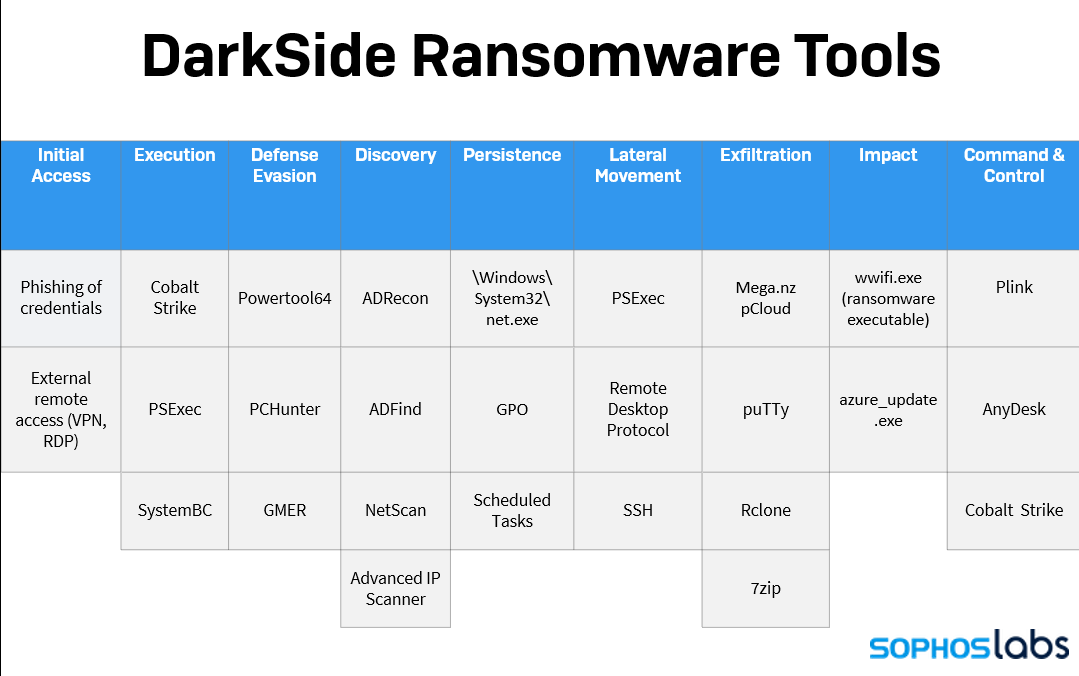
Beyond the business model, DarkSide follows generally the same tactics, techniques, and procedures of many other targeted ransomware campaigns — a mix of native Windows features, commodity malware (including SystemBC), and off-the-shelf system and exploit tools (including Cobalt Strike). This is in part because of DarkSide’s affiliate model.
The creators of DarkSide outsource the initial compromise of targets and deployment of DarkSide’s cryptographic ransomware to network penetration specialists, who hand off ransom victim “customer service” to DarkSide’s core operators. Those affiliates likely have prior experience playing the same role for other ransomware syndicates.
In Sophos’ experience in data forensics and incident response to DarkSide attacks, the initial access to the target’s network came primarily as a result of phished credentials. This is not the only way ransomware attackers can gain a foothold but it seems to be prevalent in cases involving this type of ransomware, possibly as a result of the affiliates’ preferences.
Unlike some other ransomware players, DarkSide is capable of encrypting Linux computers as well as those running Windows, which makes it a more desirable tool for threat actors who want to target large enterprises.
While some recent targeted ransomware operations from other gangs have sprung quickly, launching their attack within days, the actors behind DarkSide campaigns may spend weeks-to-months poking around inside an organization’s network before activating their ransomware payload.
Dwell Time
| Metric | Dwell Time (Days) |
| Minimum | 44 |
| Median | 45 |
| Maximum | 88 |
Over the course of that dwell time, the intruders exfiltrate as much data as possible. Darkside’s ransom notes claim the theft of large amounts of data, often from several departments within an organization, such as Accounting and R&D. Using PSExec, Remote Desktop connections, and (in the case of Linux servers) SSH to move laterally within the network, the DarkSide actors uploaded archives of stolen files to the cloud storage providers Mega or pCloud in cases we’ve investigated.
File system activity
The DarkSide ransomware performs specific steps to encrypt a document, first appending a unique file extension to the name of every targeted document type before encrypting the file.
The malware checks whether the Windows 10 user account under which it is running has administrative privileges; If it does not, the malware attempts to elevate its privileges using the CMSTPLUA technique.
DarkSide retrieves the target computer’s network adapter MAC address, and then computes CRC32 five times on the first six bytes of the adapters’ MAC address, where the initial seed is 0xDEADBEEF. Because the first six bytes of a MAC address are registered to manufacturers, many of the affected corporate machines would end up with the same file extension appended to documents simply as a result of the machines being part of a bulk purchase.
The attackers (likely the same affiliates involved in the initial access) also make an effort to terminate software that, if it was running, might otherwise interfere with the encryption process. We’ve observed them terminate the services relating to enterprise backup software from Commvault and Veeam, shut down the mail server software MailEnable, and kill SQL server database services, so they can encrypt any database they find. They also attempt to uninstall or tamper with Sophos services if they’re present on the machine. Like other ransomware, DarkSide also deletes Volume Shadow Copies, which could help recover some of the encrypted data if left unmolested.
Encrypting every document file type on a hard drive takes time, and if the process gets interrupted mid-way through, some of the unencrypted files could be recovered easily. Renaming the file with a new extension before encrypting it gives an attacker the ability to make it appear as though everything has been encrypted, as the file extension change cuts the ties between the document file type and its associated application.
The encryption process for DarkSide always has followed these steps:
| Step | Operation | Purpose |
| 1 | CreateFile (Generic Read/Write) | Open original document for reading and writing. |
| 2 | ReadFile | Read last 144 bytes of original document (look for decryption blob). |
| 3 | CloseFile | Close original document (no changes made). |
| 4 | CreateFile (Read Attributes) | Open original document. |
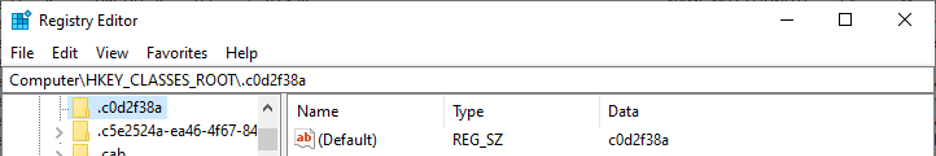
| 5 | SetRenameInformationFile | Rename document by adding a specific file type extension, for example .c0d2f38a |
| 6 | CloseFile | Close now renamed document. |
| 7 | CreateFile (Generic Read/Write) | Open renamed original document. |
| 8 | ReadFile | Read renamed original document. |
| 9 | WriteFile | Write encrypted document in renamed original document. |
| 10 | WriteFile | Add decryption blob, 144 bytes, to end of file. |
| 11 | CloseFile | Close renamed, now encrypted, document. |
Solving the ugly icon problem
There are several benefits to the threat actors when ransomware appends a new or unusual file extension to the files it encrypts. Of course, it decouples the encrypted documents from their normally associated applications, which means the user can’t interact with them in the usual way (by double-clicking). The unusual file suffixes represent both a signal to the ransomware that a file has already been encrypted (so the ransomware engine doesn’t re-encrypt or double-encrypt the same files), and carry a side benefit: it prevents other ransomware (at least, the families that target the documents they will attack using hardcoded lists of file suffixes—a lot of them) from encrypting those same files.
One downside to switching the file suffix is that, when it loses its association with its application, the document no longer uses the icon tied to that association. So an encrypted Word document, for instance, just has a blank icon rather than a pretty picture of a document with a W on it.
DarkSide appears to be very concerned with this problem of the poor appearance of encrypted hard drives, so they have worked out a solution.
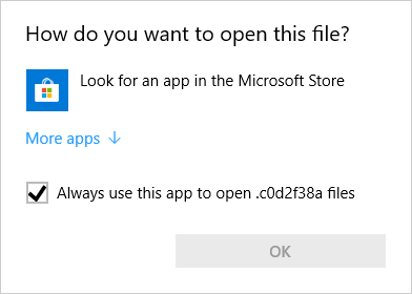
DarkSide drops an image file — an icon — into the %APPDATA%\Local directory, named after the same eight character extension the ransomware has used to rename every targeted file. In this example, that extension is .c0d2f38a. It then writes out a Windows Registry key in HKEY_CLASSES_ROOT that associates files with the unique and peculiar file extension it has generated to that icon file, so that encrypted files suddenly have a unique icon of their very own.
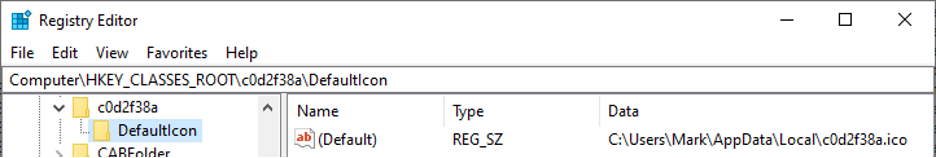
DarkSide’s .ico file is so thorough that it contains several icon sizes, so your computer will display the appropriately sized icon according to your preferences. It comes in 64×64, 32×32, 24×24, and 16×16 pixels, and it looks like a black padlock.
So what happens is that a folder full of documents goes from looking like this:
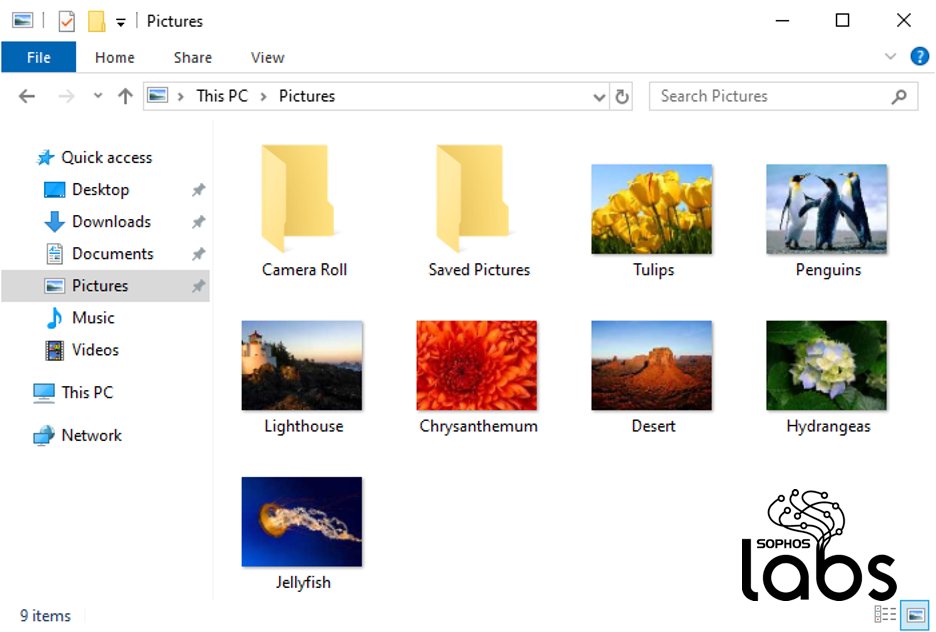
…to looking like a folder full of “locked” files, like this:
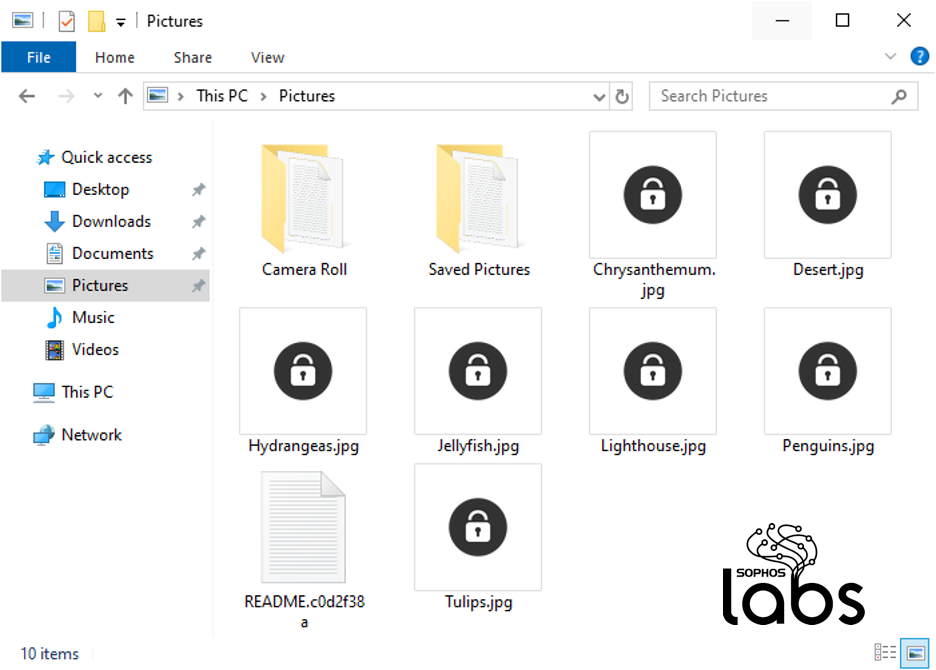
After the encryption is complete
After the ransomware has concluded the file encryption, it drops this ransom note in each folder that contains the newly scrambled files:
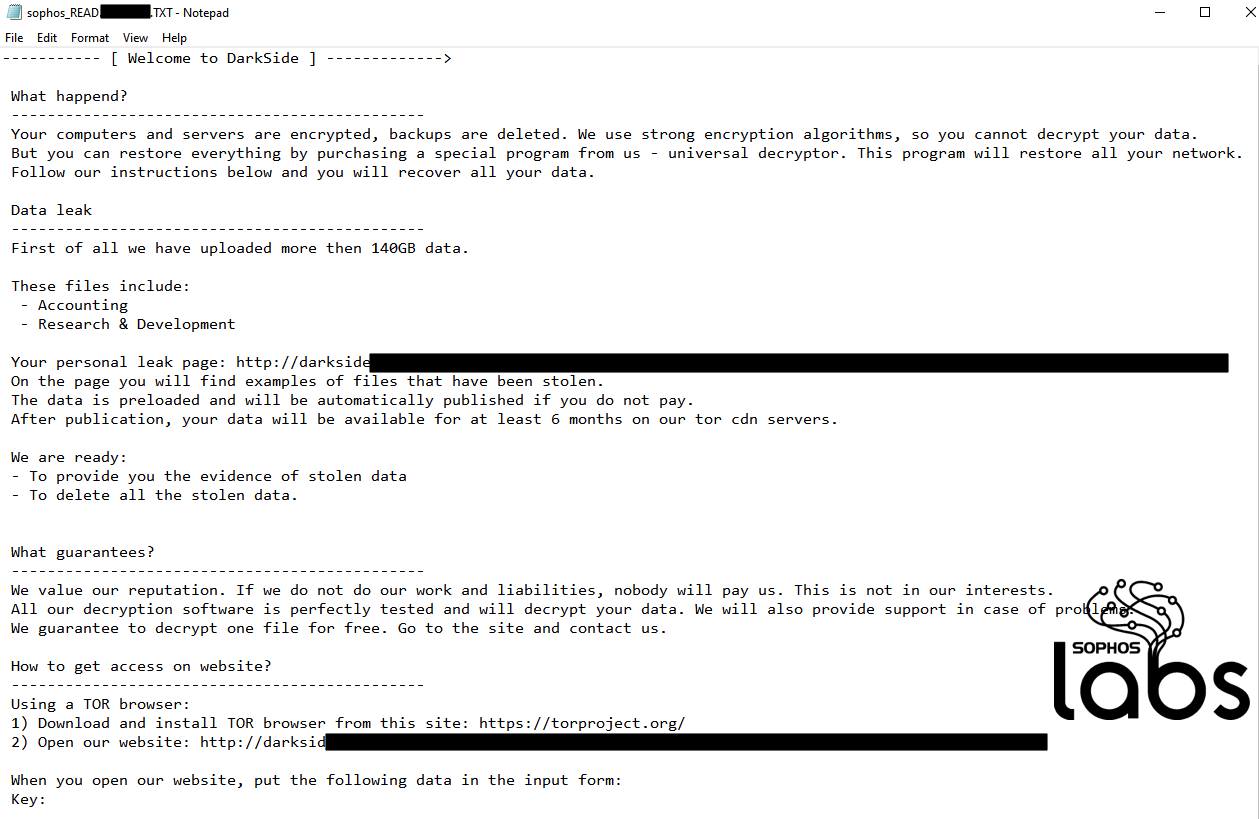
The link takes the victim to the payment page, hosted on the dark web: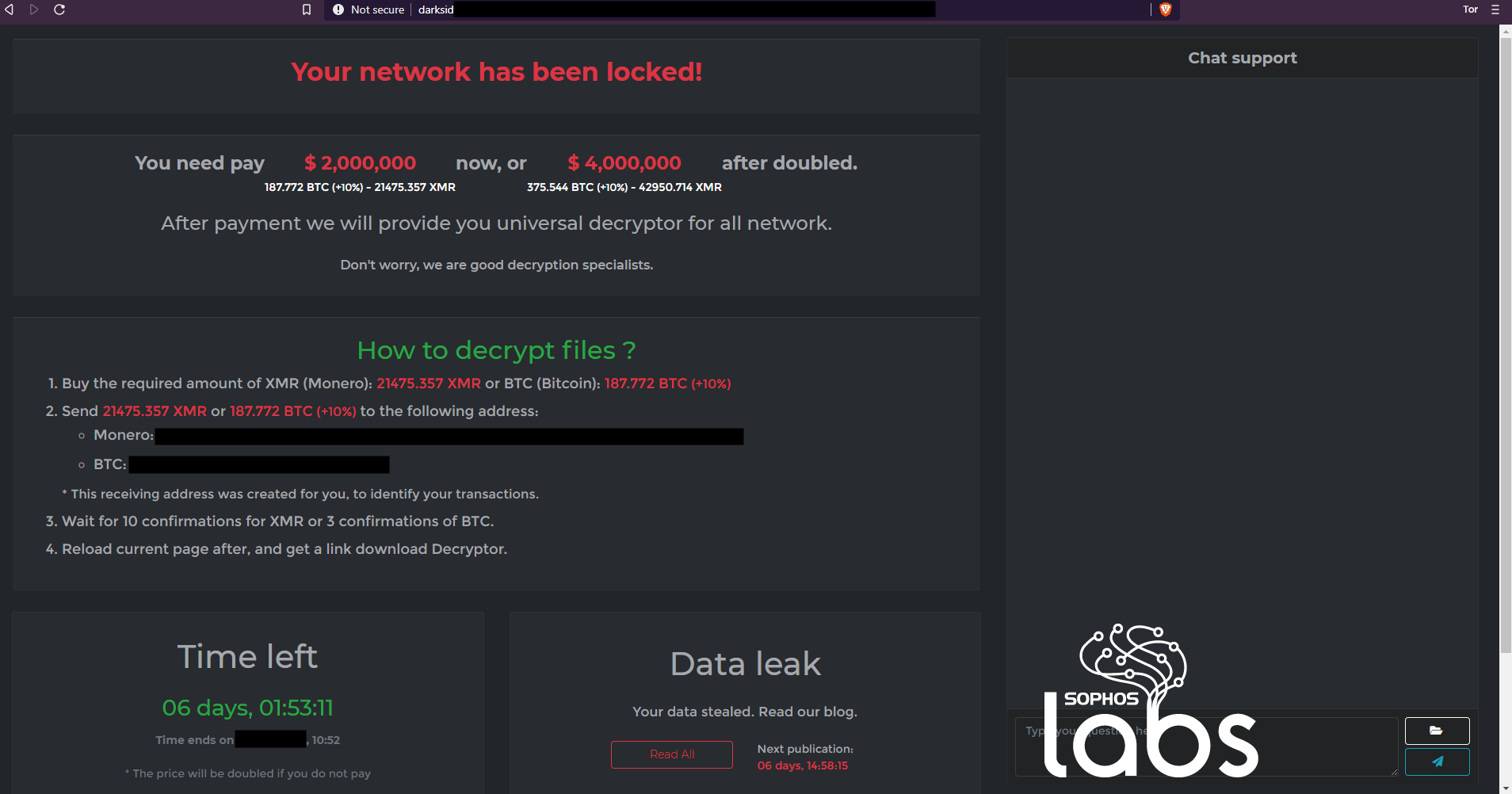
The ransom demand gives the target a handy conversion of the ransom demand into both Bitcoin and Monero (Dogecoin not currently accepted for payment), a countdown lock to when the ransom demand doubles, and a link to the page that hosts examples of “Your data stealed.”
Attacking Linux, encrypting VMDK files
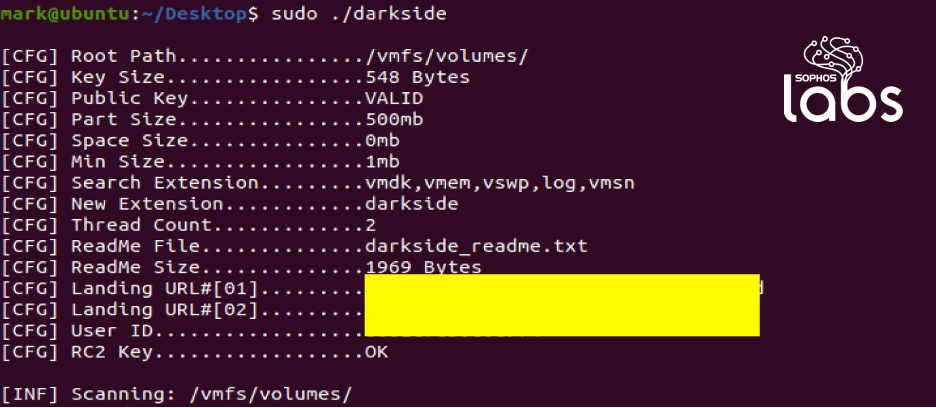
The DarkSide ransomware adversary not only attacks Windows machines, but also deploys ELF binaries (Executable and Link Format) to attack data on Linux machines. The Linux version of the DarkSide ransomware specifically targets VMDK files, which are virtual hard disk drives to be used in virtual machines like VMware and VirtualBox.
Console output of the Linux version reveals this ransomware is specifically searching for file extensions associated with virtual hard disk drives on Linux, including on hypervisor operating systems like VMWare’s ESX, where the virtual hard drives for virtual machines are stored under the /vmfs/volumes/ file path:
Turning away from the DarkSide
Sophos defends against DarkSide in multiple ways. There are behavioral and dynamic protections, which include the CryptoGuard feature in Intercept X, and both conventional endpoint detections for Windows (Troj/Ransom-GAZ, Troj/PShl-E, VBS/Agent-BGYV) and Linux (Linux/Ransm-J) malicious executables, and next-gen detections for in-memory functions (Mem/DarkSide-A, HPmal/DarkS-A) and behaviors (AMSI/Inject-H, AMSI/PSRans-A, ML/PE-A) on Windows.








